The campaign targets both Android and iPhone users through both official and unofficial channels. The infected apps were downloaded more than 242,000 times from Google Play by Android users.
While it’s not known how many iPhone users fell victim to them, the fact that the apps made it to the App Store is notable as stealer apps had never before been found on Apple’s app marketplace.

This infected app was found on both Google Play and App Store. | Image Credit – Kaspersky
The malware used an OCR plug-in made with Google’s ML Kit library to read texts from images. Images that contain relevant keywords are sent back to cybercriminals behind the malware. While the malware looks for crypto wallet recovery phrases, it can also recognise other sensitive information in images, such as messages or passwords captured in screenshots.

The SparkCat campaign targets both Android and iPhone users. | Image Credit – Kaspersky
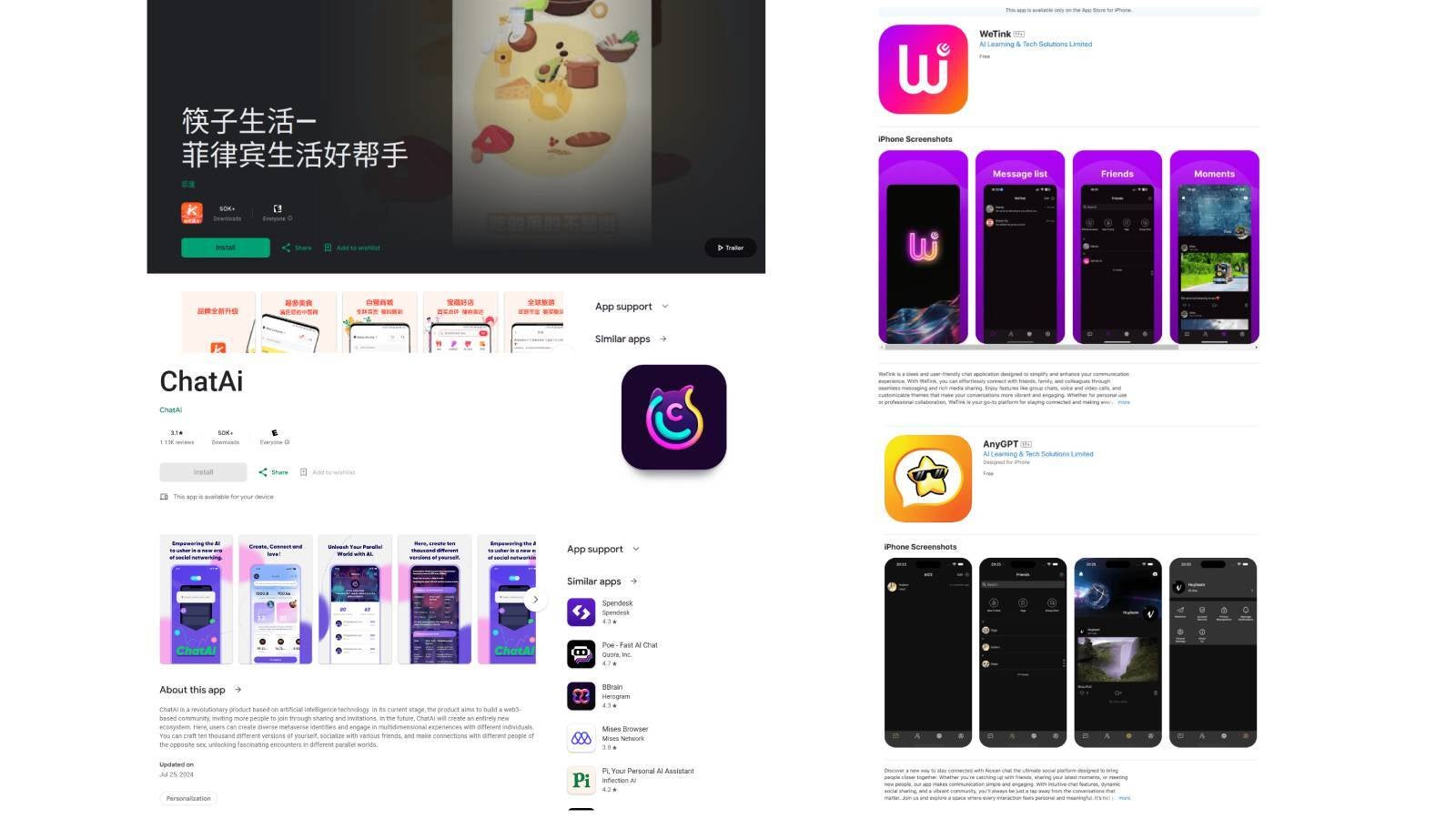
Some of the infected apps that were identified by Kaspersky include the food delivery app ComeCome, ChatAi, and messaging apps WeTink and AnyGPT. Some of the apps remain available on Google Play and App Store.
The malware has been active since March 2024. The impacted apps were hard to identify as they didn’t necessarily behave in a fishy manner and using them for the intended functionality was enough to trigger the malware without requiring excessive permissions.
Kaspersky isn’t sure whether developers are to blame for the infection or if it “was a result of a supply chain attack.” This means that while some were deliberately created to lure victims, others were legitimate apps.
The campaign appears to primarily target Android and iPhone users in Europe and Asia.
If you have any of the above-mentioned apps on your phone, be sure to delete them. To keep yourself safe from malware like these, avoid saving screenshots with sensitive data in your phone gallery.


